Injection Vulnerabilities: Learn from the latest WordPress vulnerability and why this is a major issue
Injection Vulnerabilities: Learn from the latest WordPress vulnerability and why this is a major issue
2017 has started with a tough couple of months when it comes to securing our websites. With the latest security incident of Cloudflare that caused some websites to run past the end of a buffer and return memory that contained things such as authentication tokens and HTTP cookies, plus the WordPresses security fix with version 4.7.2…let’s just say we have been busy bees trying to keep up.
Let’s talk a little more about the WordPress security fix, since it is a pretty good example of an injection vulnerability. In the OWASP top 10 list of largest web security vulnerabilities, Injection is at the top of the list. In simplest terms, an injection vulnerability is when an application is able to send an untrusted data to an interpreter. The latest WordPress security fix 4.7.2 fixed a couple of these injection vulnerabilities.
WordPress security fix 4.7.2 was initially announced as a fix for a WP_Query vulnerability to SQL Injection (SQLi) when plugins and themes were potentially using it in the wrong way. A cross-site scripting (XSS) vulnerability was also discovered in the posts list table. But there was one major vulnerability they did not disclose right away (so that they could give people time to update first before it was disclosed to the world) and that vulnerability was an Unauthenticated Privilege Escalation Vulnerability in a REST API Endpoint. This affected version 4.7 and 4.7.1 which made the new REST API enabled by default even more of a risk for websites. It also has been said by WordPress that this was not a vulnerability in versions prior to 4.7 and that includes the plugin version that was being developed before they rolled it into the WordPress core.
REST API
Before we get into what this vulnerability was, let’s explain a little more about what a REST API is. REST stands for Representational State Transfer or RESTful web services. Basically, developers will develop a RESTful API to allow other websites, mobile applications, desktop and server software to retrieve, create, update and delete data without having to actually access the website from a browser.
WordPress started developing the REST API infrastructure in version 4.4 and the actual REST API could be tested in the plugin we referenced earlier. WordPress wants to push forward to become what they say is a fully-fledged application framework and not just a blog engine like what people used to think of WordPress.
What was the vulnerability?
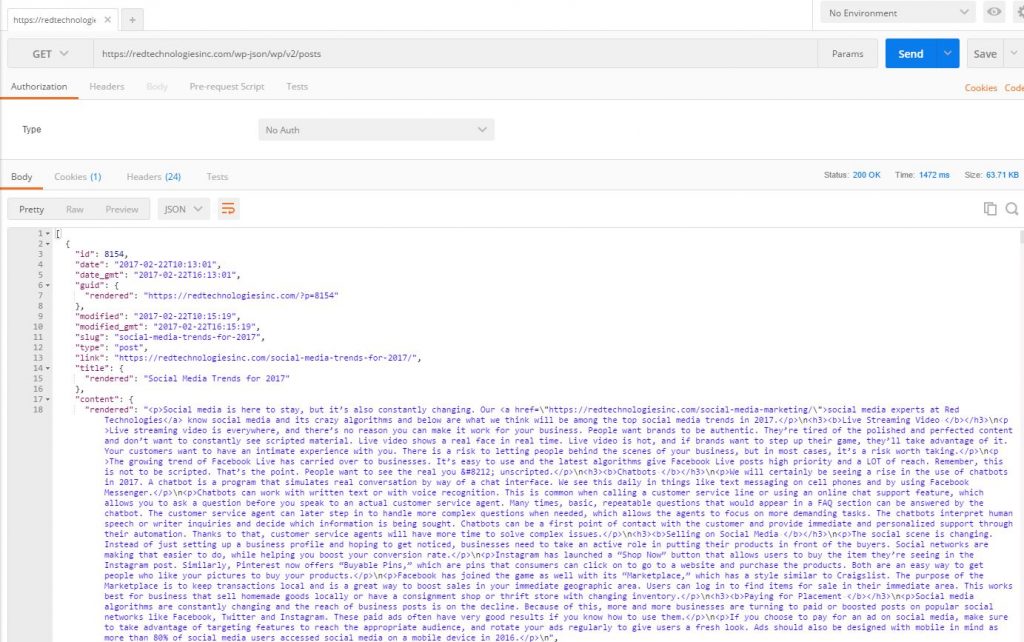
By default anyone can use tools like POSTMAN to make requests to a person’s WordPress website as you can see below.
The above screenshot is nothing more than what is already public on the Red Technologies website just in a more easily parsed and understandable format for other applications. In fact, this particular example is our latest blog post about social media trends of 2017.
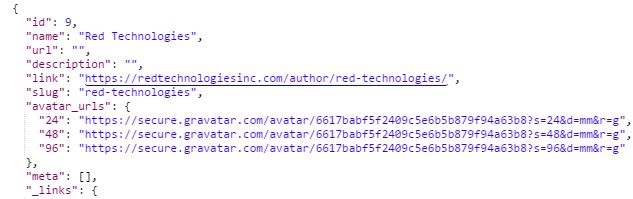
You can also return users who have previously posted content using the endpoint /wp-json/wp/v2/users like the below screenshot.
Besides retrieving data, you can use the REST API to update data on WordPress. Though this can only be done if you are authenticated. This is where we run into the vulnerability recently fixed.
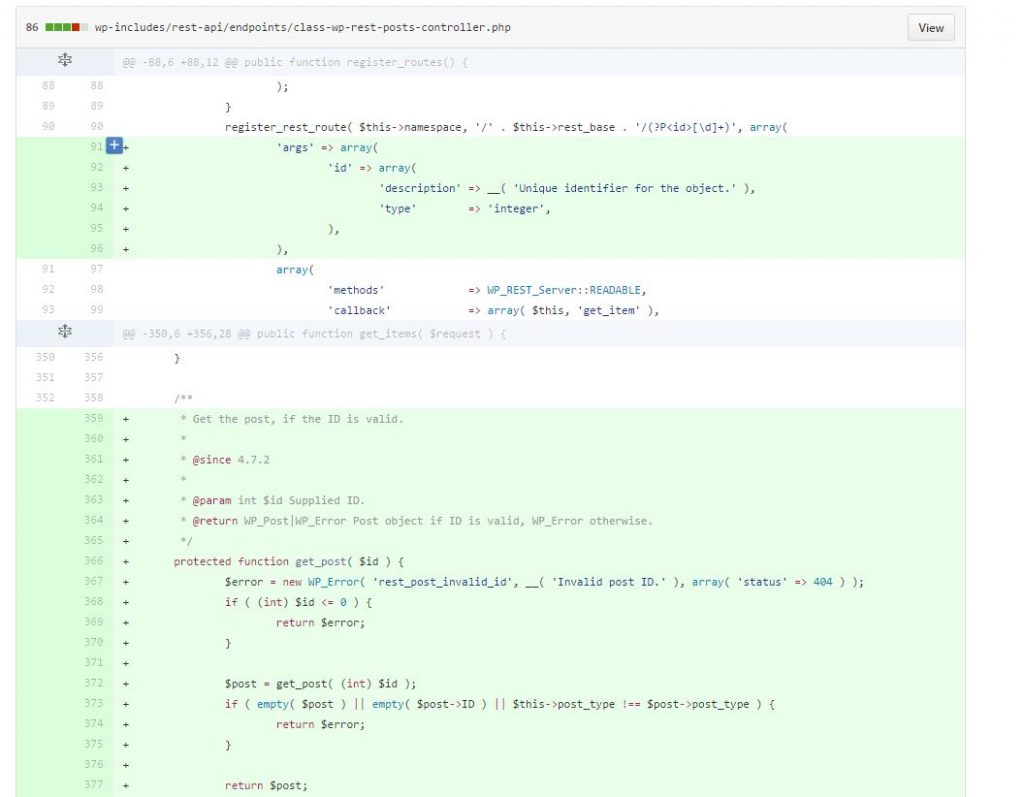
In the file /wp-includes/rest-api/endpoints/class-wp-rest-posts-controller.php and other endpoint files, there was a vulnerability in the way an update_item method casted the ID parameter to an integer. As Sucuri (who found this vulnerability) has stated, the issue is in how PHP handles type comparisons and conversions. The PHP documentation states they do not “support explicit type definition in variable declaration; variable’s type is determined by context in which the variable is used.” So before this issue was fixed, you could use the example of /wp-json/wp/v2/posts/12?id=34YouAreHacked and it would allow you to start injecting data into the post that has the ID of 34.
Thankfully, because of the excellent security team at Sucuri, WordPress developers were notified and it was patched by ensuring the ID parameter is properly cast to integers. If you actually enjoy looking at how the WordPress team fixed this issue as we like to do, you can see how they fixed this in the screenshot below or visit their GitHub repository.
 With this vulnerability, some researches have estimated that there were over 800,000 attacks within the first couple of days the vulnerability was disclosed.
With this vulnerability, some researches have estimated that there were over 800,000 attacks within the first couple of days the vulnerability was disclosed.
Is there anything I can do to disable the WordPress REST API?
Many people are asking why the API is enabled by default. WordPress is standing by its decision to keep the REST API enabled by default. It wants more of the admin side to depend on the REST API as well as push developers to depend more on the API for their themes and plugins. One of the developers at WordPress stated in this ticket that turning off the API would be the same as turning off the admin-ajax.php file and both would break the site.
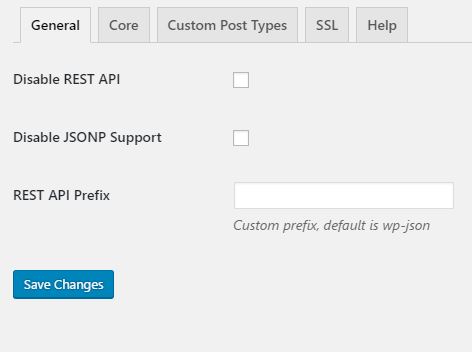
Fortunately there are a few things you can try. You can install either Disable REST API, which essentially forces an authentication on all endpoints before you can use the API, like the screenshot below.
If you want more control and you do not want to force an authentication for every endpoint, you can try out the REST API Toolbox plugin. We have tried both and so far both seem to work very well. As you can see in the below screenshots, you have much more control over what you turn on or off. For example, you can disable the entire REST API, change the REST API Prefix, turn off just certain endpoints, or require authentication for certain endpoints. But keep in mind that if you turn off endpoints it could break certain functionality of your site and plugins. Red Technologies suggests that if you want to turn certain REST API functions “off,” then require them to be authenticated so that the admin side can still use the endpoints.
Again, as we always try to express, keep your WordPress sites, plugins and themes up to date as much as you can.
If you have a WordPress website, we can help keep your site protected. To learn more about the WordPress Security & Maintenance Services that Red Technologies provides, visit What We Do or give us a call at 612-310-7972.
Disclaimer: We are not certified security experts. We are giving a high-level overview about web security so that you can be more informed about some of the most common security vulnerabilities to look out for when developing or finding a developer. We will also be sharing some resources to help you continue your research on web security.