And now a word from our technical side…
Ransomware, What is it? Should I be Concerned?
Ransomware at its basic level is among the most malicious forms of malware to target a variety of businesses and individuals. Although most ransomware targets medical facilities, schools, state and government agencies, your small business and personal files are just as susceptible to this form of attack as the larger corporations.
What is Ransomware?
Ransomware has been around for a very long time and their methods can come in all sorts of different ways, but they all share the same common elements. Malware that in some way prevents the user from accessing their files by locking their screen or files and demanding payment (usually in the form of bitcoin so the payment is untraceable). They hold your files for ransom until you pay said ransom. Before 2013, many forms of Ransomware locked your screen and showed a spoofed law enforcement agency notice to users. They would accuse the victim of something illegal to scare them into paying to unlock their computer. Many security experts were able to find ways to remove the malware without paying these ransoms so organizations and individuals were able to gain access to their computer.
Around 2013, these malicious hackers upped their game with a new variant of ransomware. With this variant, when the user would open an infected file it would immediately start to encrypt all files on the system, making every file on your computer unusable unless you paid the ransom and they would give you a private key to decrypt the files on your system. The newest forms of ransomware can not only encrypt your computer but also all unmapped network shares and in some cases even mapped network shares, causing havoc on your business or life by encrypting valuable files.
The most recent form of this is called “Locky,” which most notably comes in the form of emails usually using a similar subject like “ATTN: Invoice K-1456621” and in the body of the email would be a message stating something like “Please see the attached invoice and remit payment according to the terms listed at the bottom of the invoice.” Many of these files are Microsoft Word or Excel documents. Once the user opens this document it will look like a bunch of random characters and symbols and the victim will be prompted to enable macros in the document.
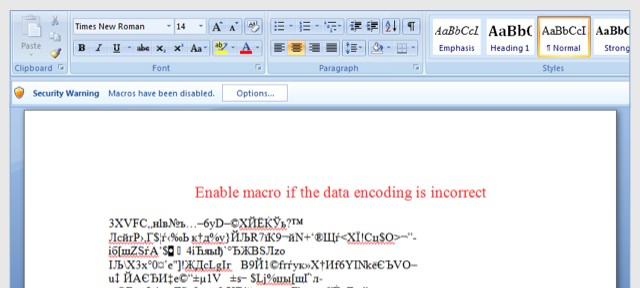
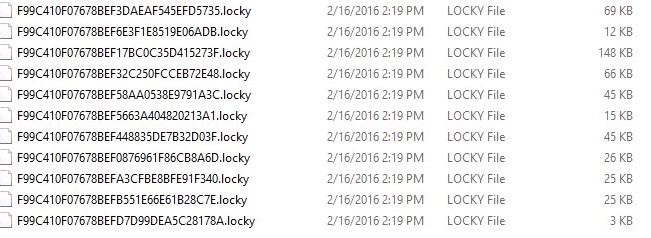
Once the user enables macros the file will immediately download a malicious file from a remote server that starts to encrypt his or her computer’s files and any attached drives. The “Locky” form of ransomware encrypts all the files and will add the “.locky” extension to the encrypted files. Making it virtually impossible to gain access to any of your computers’ files without the private key.
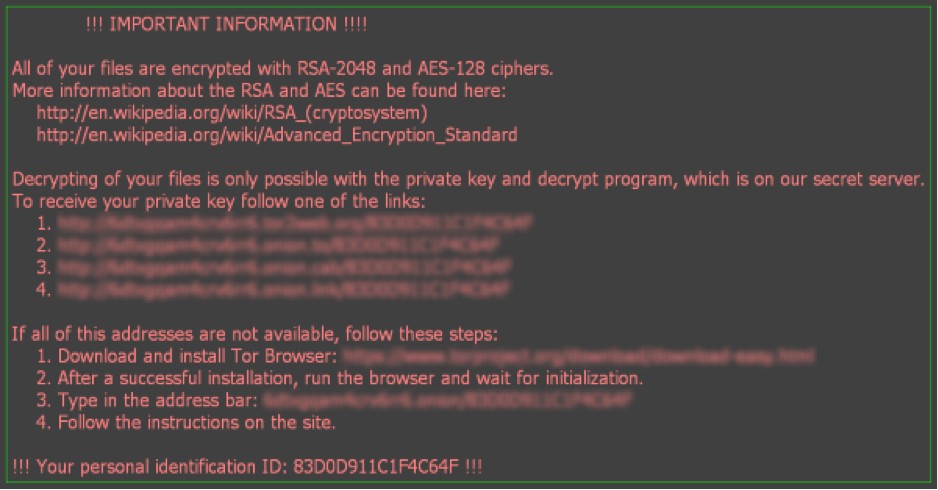
Once the files are encrypted and renamed, you may get a message telling you all your files are encrypted and that decrypting your files is only possible with the private key along with links to visit with instructions in how to decrypt your files. When you visit these links, you will get a website with instructions on how to pay for your private key. Most of the time even if you pay for these private keys a lot of the time it will only decrypt part of your drives. They keep demanding more and more money to fully decrypt your all your files.
The best defense for these types of attacks are to train your staff to spot any suspicious emails or files that come from anyone you may not know or even people you may know that could have had their emails spoofed or stolen. Also, never visit these links if you do run into this situation as it is a good way to notify the hacker that they have a live one to target, they will more than likely up their ante on targeting you or your business.
Ransomware is now targeting websites
Many people may have heard about ransomware coming in through emails but now many businesses are seeing their websites being targeted for ransomware. It can infect a website in a few different ways. For example, it could infect the website in such a way that when a user visits one of these infected websites,it will immediately start downloading the infected file or files to the end user that starts to encrypt the end user’s computers. Or it could infect the website giving access to the hackers to gain access to the website, allowing them to deface the homepage and encrypt all files on the web server. What is even worse is the malware can spread across the web server or environment encrypting other websites on that server or connected drives.
We are also seeing companies with applications such as help desk applications that take in files through either web forms or emails that are directly put into their applications, making it even harder for the end user to detect if the attached files are infected with malware or not, bypassing email spam filters and malware detection.
What Can I do to help prevent Ransomware?
One of the most important forms of protection is an easy one. Educate your staff and self on how to keep an eye out for these emails and attached files. If you do not know the person sending you attached files never open the files. And if you do end up opening a file you are not sure about, make sure to never enable macros on a document such as Word or Excel. You may want to put your end users through a course such as the one offered through security expert Troy Hunt and security software company Varonis Free Ransomware Course.
Second most important form of protection is to make sure you regularly backup all files on your computer and servers. If you do get infected with Ransomware at least you are able to restore from the most recent backup and not have to deal with trying to pay these malicious hackers giving them more support to keep infecting other businesses and individuals.
Always remember to keep your computers, servers, and websites up to date with the latest software and plugin updates. This will help patch the holes or vulnerabilities in the software or website plugins that may allow for these attacks to take place.
Be very cautious of any attachments or uploaded files, especially Microsoft office email attachments that asks you to enable macros. NEVER enable macros, instead immediately delete the file. If it is still in your email, report it as spam so your email provider such as Gmail or some other email provider can learn to detect these malicious emails. The more you report these as spam the better these systems can learn to detect them as malicious and send them to quarantine or spam.
If you are hosting your own website or email servers, it is good to invest in a layered defense such as Intrusion Prevention System which can help gather and identify data and behavior on the network layer and help block the malicious activity including allowing those macros to communicate with the remote servers and allowing them to download the malicious programs that can encrypt all your files. Also, implementing a web application firewall which works at the application layer by helping prevent things such as common attacks as Cross-site scripting (XSS) or code injection that can help compromise your system or website application.
If you have a WordPress website, we can help keep your site protected. To learn more about the WordPress Security & Maintenance Services that Red Technologies provides, visit https://redtechnologiesinc.com/what-we-do or give us a call at 612-310-7972.
Disclaimer: We are not certified security experts. We are giving a high-level overview about web and file security so that you can be more informed about some of the most common security vulnerabilities to look out for when developing or finding a developer. We will also be sharing some resources to help you continue your research on web security.




